Microsoft published an advisory about a new font parsing vulnerability in Windows on March 23, 2020. The company rated the vulnerability as critical and said that it was aware of limited targeted attacks exploiting the vulnerability.
Microsoft listed several workarounds to mitigate attacks but they all reduced functionality for users in one way or another.
Microsoft has yet to release a security patch to address the issue for all versions of Windows affected by the vulnerability.
Security company 0Patch, well-known for its pledge to create and distribute patches for the Windows 7 and Windows Server 2008 R2 operating systems that ran out of official support this year. While business and Enterprise customers may extend support by up to three years, home users cannot officially and 0Patch patches.
Microsoft already announced that it won’t provide the font parsing patch for unsupported versions of Windows 7 while it will provide it to companies and Enterprise organizations that have joined the ESU program to receive extended support updates.
0Patch announced today that it has created a micro-patch for the font parsing vulnerability that affects all major client and server versions of the Windows operating system.
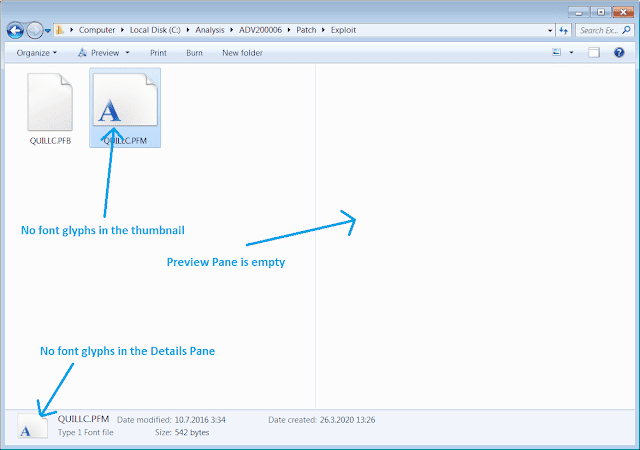
A blog post on the official 0Patch blog lists the official information and analyzes the workarounds that Microsoft posted. While all work to a degree, all have disadvantages that 0Patch highlights. Disabling the preview pane, details pane and thumbnails in Windows Explorer for example only blocks attacks when the file manager is used but it won’t protect against other attack vectors.
The team analyzed the vulnerability — it had to since Microsoft did not disclose details about it — and found a solution that it turned into a micro patch.
Basically, what 0Patch did was put a bouncer in front of font operations if Adobe Type 1 Script fonts are used so that the vulnerability cannot be exploited.
So we decided to find the common execution point that various Windows applications such as Windows Explorer, Font Viewer, and applications using Windows-integrated font support are using to pass a font to Windows, then place a bouncer there that would keep Adobe Type 1 PostScript fonts out.
The blog post goes into detail and users interested in additional details may check it out for additional information on the implementation.
All administrators need to do is install the micro patch on the device to protect it against the vulnerability.
With this micropatch in place, all applications using Windows GDI for font-related operations will find any Adobe Type 1 PostScript fonts rendered invalid and unable to load. For example, Windows Explorer will start looking like this when viewing a folder with a pair of otherwise valid PFM and PFB files.
The patch is available for free for Windows 7 64-bit and Windows Server 2008 R2 without Extended Security Updates. 0Patch plans to create patches for ESU versions of Windows 7 and Windows Server 2008 R2, as well as Windows 8.1 and Windows Server 2012 soon as well.
Windows 10 and Server won’t receive the patch as these systems face less of a risk from the vulnerability than previous versions of Windows.
