Until Microsoft releases a patch for two critical vulnerabilities affecting the font parsing component in all supported versions of Windows, some users can apply temporary protection in the form of a micropatch that prevents exploitation.
The two flaws affect the Adobe Type Manager Library (maintained by Microsoft) and are in the ATMFD.DLL font driver that processes Adobe Type 1 PostScript and OpenType fonts.
Leveraging them on systems earlier than Windows 10 can lead to remote code execution with elevated privileges. Microsoft is aware of threat actors exploiting them in targeted attacks on older versions of the operating system.
Works against remote attackers
Microcode that mitigates the risk of exploitation is available for Windows 7 64-bit and Windows Server 2008 R2 that do not benefit from Microsoft’s Extended Security Updates (ESU). It is delivered automatically through the 0Patch platform – for both paying and non-paying users – and can be applied without rebooting the machine.
Thus, for the time being, Microsoft’s least supported operating system is the only one getting a temporary fix for the font parsing bugs the company disclosed on March 23.
In Windows 10 v1709, font parsing happens in an isolated space, making exploitation more difficult. On earlier versions, though, this happens in the kernel, providing attackers an opportunity to run code with the highest privileges.
The 0Patch fix will become available for Windows 7 and Windows Server 2008 R2 with ESU, Windows 8.1 and Windows Server 2012, both 32-bit and 64-bit.
It should be noted that these vulnerabilities can be exploited by a remote adversary and this threat vector is what the micropatch protects against. A local attacker can bypass the 0Patch fix by writing code that makes system calls to the kernel.
Visible effects
In a blog post on Thursday, Mitja Kolsek, CEO of Acros Security company behind 0Patch, provides the full code of the micropatch and explains how it works.
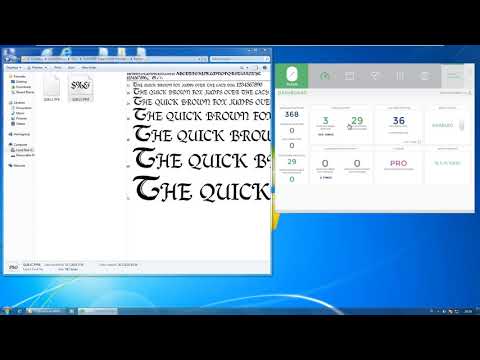
“With this micropatch in place, all applications using Windows GDI for font-related operations will find any Adobe Type 1 PostScript fonts rendered invalid and unable to load” Mitja Kolsek
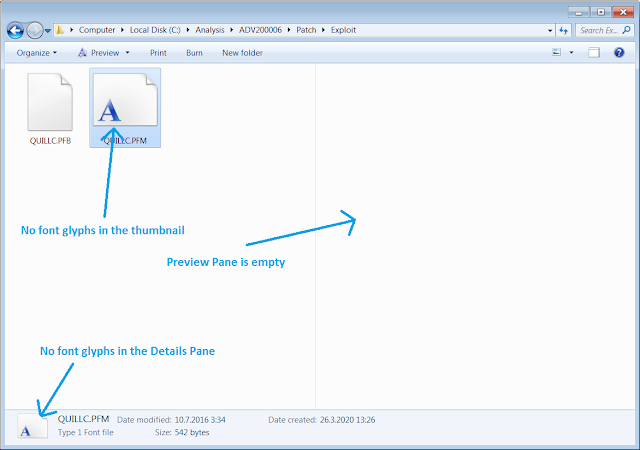
Basically, Windows’ Explorer will no longer show a preview of .PFM and .PFB font file after applying the temporary fix. The glyphs won’t be rendered in the Preview Pane, as thumbnails or in the Details Pane.
Other font types that are not parsed with the vulnerable component remained unaffected.
Microsoft has provided three workarounds that can mitigate the problem, each with its advantages and disadvantages:
| Workaround | Applicability |
| Disable the Preview Pane and Details Pane in Windows Explorer | Works on all systems but won’t mitigate the issue if you open a document with the vulnerable font class |
| Disable the WebClient service | Works on all systems but won’t mitigate the issue if you open a document with the vulnerable font class |
| Rename ATMFD.DLL | Only works on older (before Windows 10) but completely mitigates the issue though can introduce usability issues in rare cases |
Below is a video showing how Windows behaves with and without the microcode from 0Patch: