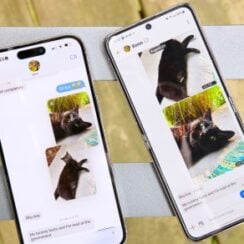
One of the big draws of iPhone and Mac is the iMessage software. This texting app makes it easy to stay connected to friends and family, and many users point to it as a key reason they stay within the Apple ecosystem – venture off to …
Rita El Khoury / Android Authority One Gmail inbox for everything we need TL;DR Gmail is working on a subscription management feature that promises to help you declutter your inbox. The feature will intelligently categorize senders by email frequency, making it simple to spot potential spam …
OnePlus and OPPO have partnered with Google to integrate Gemini into their devices. Both brands have assured that Gemini Ultra-based AI features should start rolling out to their devices by the end of this year. OnePlus and OPPO recently introduced the AI Eraser, and with this …
Today, TEAMGROUP has launched the T-CREATE EXPERT R31 3-in-1 Card Reader. Designed with portability in mind, the EXPERT R31 measures just 8.5 cm and is lightweight, making it easy to carry and access creative content wherever inspiration strikes. The T-CREATE EXPERT R31 is equipped with a …
(Image credit: Bungie) Following quite an impressive livestream showcase for the upcoming Destiny 2: The Final Shape expansion — it revealed that the DLC is bringing a special Prismatic multi-classing subclass to the game, along with Exotic class items for it that drop with combinations of …
The Arduino open-source platform is an excellent way to create your own home and hobby electronics projects from scratch. The logic boards sold under the Arduino brand are receptive to all kinds of stimuli and inputs, allowing you to create Arduino projects ranging from air monitors …
At Intel’s Vision 2024 event, which is held in Phoenix, AZ, has seen several key announcements. Still, perhaps one that has flown under the radar is their 6th Generation Xeon platform built on their Intel 3 node, which is aptly named Intel Xeon 6. It is …
Forget grainy footage and shaky home videos, the Online world is currently craving for crisp and high-quality visuals! That’s where Winxvideo AI comes in, wielding the power of artificial intelligence to transform all your videos from forgettable recordings to fantastic visual experiences. Developed by the innovative …
TRIBIT has launched its XSound Plus 2 Portable Bluetooth Speaker, an upgraded iteration of the MaxSound Plus. The new model boasts several enhancements over its predecessor, including an additional 6W of power, an extended playtime of 4 hours, Bluetooth 5.3, the introduction of Party Mode, and …