
Cybercriminals are distributing malware using fake security certificate update requests displayed on previously compromised websites, attempting to infect potential victims with backdoors and Trojans using a malicious installer.
The attackers bait their targets with a “NET::ERR_CERT_OUT_OF_DATE” error message presented within an iframe displayed over the site’s actual contents and asking them to install a security certificate that to allow their connection to succeed.
Security certificates (also known as digital certificates or identity certificates) are issued by Certification Authorities (CAs) and used to encrypt the communication between a user’s browser and a website’s server.
When digital certificates are out of date and not renewed, web browsers display a notification letting the users know of the decrease in the security of their connection to the website.
Malware campaign active for at least two months
Security researchers at Kaspersky have found the earliest signs of this campaign to be dating from January 16, 2020, with various types of websites being compromised and used to deliver malware to victims, from auto part stores to the site of a zoo.
“The alarming notification consists of an iframe — with contents loaded from the third-party resource ldfidfa[.]pw — overlaid on top of the original page,” the researchers found. “The URL bar still displays the legitimate address.”
The code injected by the operators behind this campaign as a jquery.js script overlays the malicious iframe with the exact same size as the compromised webpage.
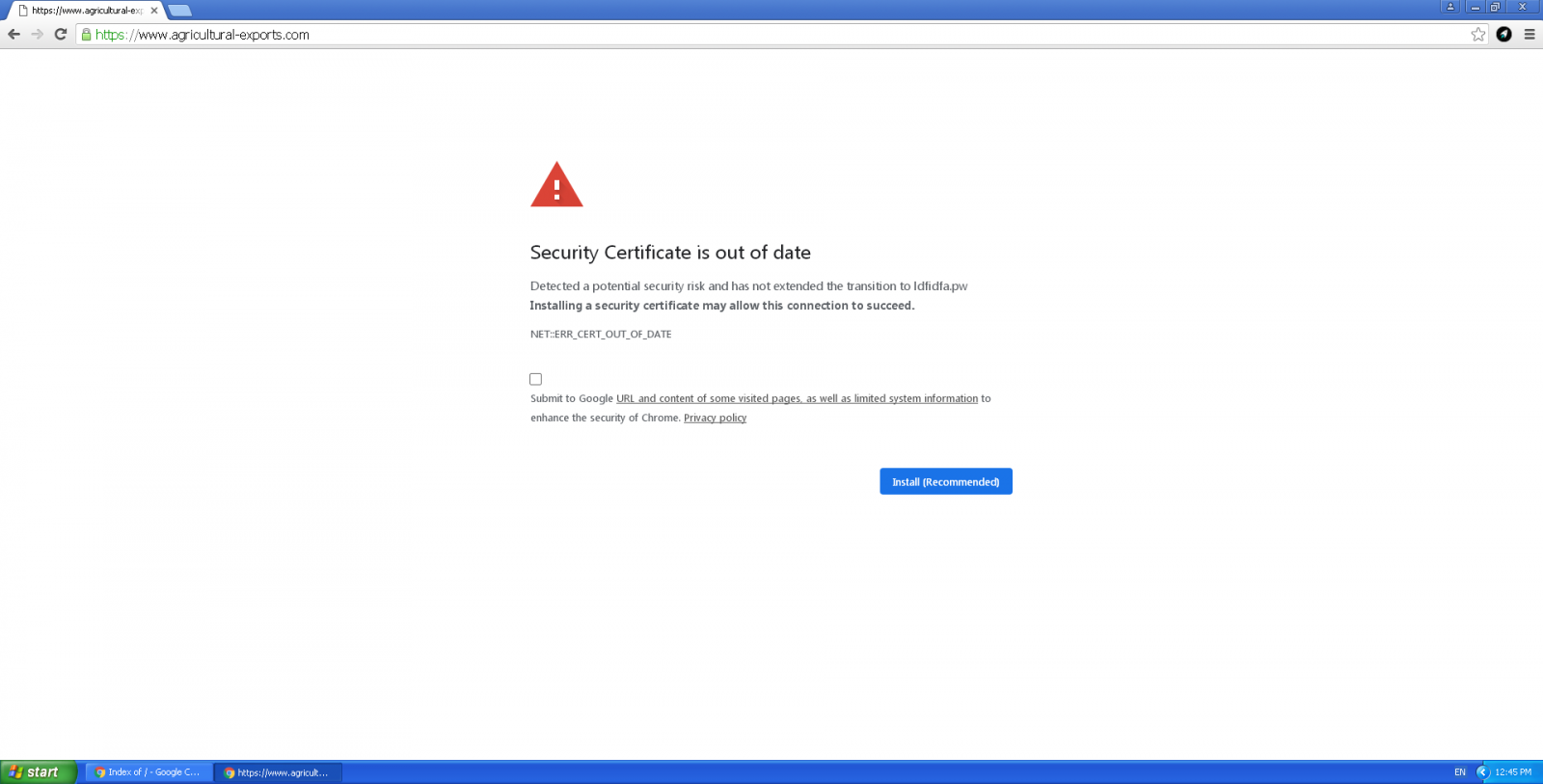
“The iframe content is loaded from the address https[:]//ldfidfa[.]pw//chrome.html,” the researchers add. “As a result, instead of the original page, the user sees a seemingly genuine banner urgently prompting to install a certificate update.”
If the targets fall for the attackers’ tricks and click the “Install (Recommended)” button under the fake warning message, they will download a Certificate_Update_v02.2020.exe binary that will infect them with malware instead of solving the made-up security certificate error.
Kaspersky discovered while monitoring these attacks that the victims will get infected either with the Buerak Trojan downloader that will download and install more malware onto infected computers.
The Mokes backdoor was also spread as a malicious payload during early-January and used by the attackers to download additional malware, to steal the victims’ user credentials, capture keystrokes, records ambient audio every 5 minutes, as well as take screenshots and intercept information entered in the web browser.
More details about this campaign and indicators of compromise (IOCs) including malware hashes and command-and-control server domain info are available at the end of Kaspersky’s analysis.
