From late 2019, MAZE Ransomware started becoming infamous for its Encryption, data stealing and the subsequent selling of the stolen data. Few other reasons behind its popularity are also its unique targets and the ransom demands.
From its inception around May 2019, MAZE actors are targeting multiple sectors, prominent ones being healthcare and research, that hold sensitive data — government and private firms are also hot targets for this ransomware. In multiple instances, attackers have posed themselves as government agencies or security vendors asking users to open the attachments in emails/websites — in some instances, the victim machines were breached already, much before the actual ransomware attacks. The ransom demands by the Maze group vary depending on the data acquired from a compromised network (victim) and the victims’ ability to pay. These demands were mostly in bitcoins ranging from a few hundred to a few million dollars.
Maze has been using emails, RDP along with exploit kits like Fallout EK, Spelevo EK which were using some Adobe Flash player and Internet Explorer vulnerabilities (e.g. CVE-2018-8174, CVE-2018-4878 and CVE-2018-15982). Although these are past cases, there’s a possibility now that MAZE actors may use other vectors to carry out a fresh wave of attacks.
Here is a typical Ransom Note used by Maze Ransomware. This Ransom Note is dropped in every encrypted folder.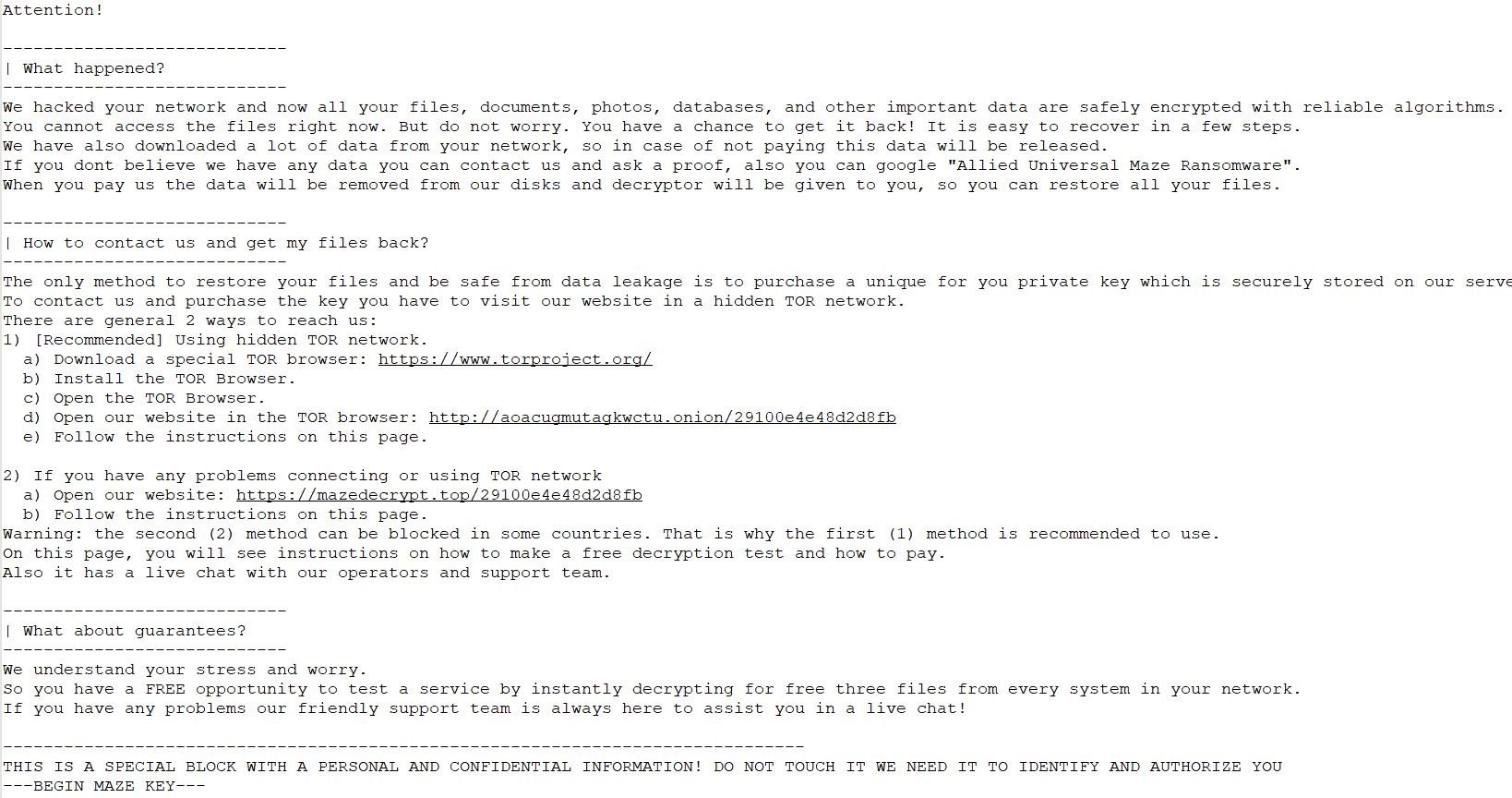
Ransom Note
After a successful attack, if the victim does not respond to ransom demands, adversaries either publish the encrypted data or sell it on underground forums.
Quick Heal products are equipped with multilayered detection technologies like IDS/IPS, DNA Scan, Email Scan, BDS, Web Protection and Patented Anti Ransomware detection. This multi-layered security approach helps us in protecting our customers against Maze Ransomware and other known, unknown threats efficiently.
Precautionary measures:
Common infection vectors used by Maze Ransomware are phishing emails with MS Office attachments and fake/phishing websites laced with Exploit Kits. Hence, we advise our end users to exercise caution while handling emails from unknown sources, downloading MS Office attachments, enabling macros and clicking on suspicious links.
Here are a few additional guidelines which will help to minimize the attack surface & possible damage to IT infrastructure.
Patch the OS and Software:
- Keep your Operating System and other software updated. Software updates frequently include patches for newly discovered security vulnerabilities which could be exploited by attackers.
- Apply patches and updates for software like Microsoft Office, Java, Adobe Reader, Adobe Flash, and Internet Browsers like Internet Explorer, Chrome, Firefox, Opera, etc., including Browser Plugins
- Always keep your security software (antivirus, firewall, etc.) up to date to protect your computer from new variants of Malware.
- Do not download cracked/pirated software, as they risk backdoor entry for malware into your computer.
- Avoid downloading software from untrusted P2P or torrent sites. In most cases, they harbor malicious software
Users & privileges:
- Audit ‘Local /Domain Users’ and remove/disable unwanted users.
- Change passwords of ALL user accounts & set unique complex passwords (which includes letters in UPPER CASE, lower case, numbers, special character’s that are never used before). However, a bad example would be common passwords like P@ssw0rd, Admin@123#, etc.)
- Set password expiration & account lockout policies (in case the wrong password is entered).
- Don’t assign Administrator privileges to users.
- Wherever possible, enable Multi-Factor authentication to ensure all logins are legitimate.
- Don’t stay logged in as an administrator, unless it is strictly necessary.
- Avoid browsing, opening documents or other regular work activities while logged in as an administrator.
Disable macros for Microsoft Office:
- Do not enable ‘macros’ or ‘editing mode’ by default upon execution of the document, especially for attachments received via emails. A lot of malware infections rely on your action to turn ON macros.
- Consider installing Microsoft Office Viewers — these viewer applications let you see what documents look like without even opening them in Word or Excel. More importantly, the viewer software doesn’t support macros at all, so this reduces the risk of enabling macros unintentionally.
Keep your Antivirus software and signatures updated:
- From the security side of things, it is certainly beneficial to keep antivirus and other signature-based protections in place and up to date.
- While signature-based protections alone are not sufficient to detect and prevent sophisticated ransomware attacks designed to evade traditional protections, they are an important component of a comprehensive security posture.
- Up-to-date antivirus protection can safeguard your organization against known malware that has been seen before and has an existing and recognized signature.
- Respond carefully & sensibly to the alerts raised by Behavioural-based detection system and Anti- Ransomware Protection systems. Prefer to block/Deny unknown application detected by these systems.
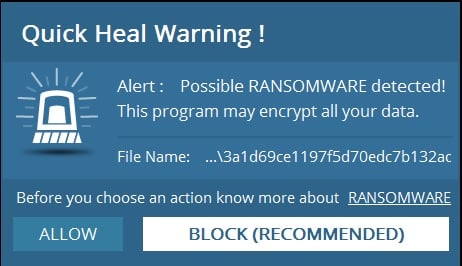
Representative image of a User Decision prompt from heuristic detection modules
Secure Browsing:
- Always update your browser
- Try to avoid downloading pirated/cracked media or software from sites like torrents.
- Block the ad pop-ups in the browser.
- Always verify whether you are accessing the genuine site by checking the address bar of the browser. Phishing sites may show contents like a genuine one.
- Bookmark important sites to avoid being a victim of phishing.
- Do not share your details like name, contact number, email id, social networking site credentials for any unknown website.
- Do not install extensions in browsers which you are not fully aware of. Lookout for impersonating webpages and do not allow any prompt on an unknown web page that you are visiting. Avoid visiting crack software download websites
Network and Shared folders:
- Keep strong and unique passwords for login accounts and network shares.
- Disable unnecessary, admin share. i.e. admin$. Give access permission to shared data as per requirement
- Audit RDP access & disable it if not required. Else, set appropriate rules to allow access from only specific & intended Hosts.
- Attackers, in almost all cases, use PowerShell scripts to exploit the vulnerability, so disable the PowerShell in the Network. If you require PowerShell for internal use, then try to block the PowerShell.exe connecting to public access.
- Audit gateway system & check for misconfiguration, if any. (E.g. Improper forwarding done, if any)
- Use a VPN to access the network, instead of exposing RDP to the Internet.
- Create a separate network folder for each user when managing access to shared network folders and disable if found unnecessary.
- Don’t keep shared software in executable form.
Back up your data and files:
- It’s vital that you consistently back up your important files, preferably using air-gapped storage [which is physically isolated from unsecured networks]. Enable automatic backups, if possible, for your employees, so you don’t have to rely on them to remember to execute regular backups on their own.
- Protect all backups with a unique complex password (mentioned in users and privileges).
- Always use a combination of online and offline backup.
- If your computer gets infected with ransomware, your files can be restored from the offline backup, once the malware has been removed.
- Do not keep offline backups connected to your system as this data could be encrypted when ransomware strikes.
Email Security:
- Strengthen email security to detect harmful attachments
- Enable Multi-Factor authentication to ensure all logins are legitimate
- Set password expiration & account lockout policies (in case the wrong password is entered)
- Don’t open attachments and links in an email sent by an unknown, unexpected or unwanted source. Delete suspicious-looking emails you receive from unknown sources, especially if they contain links or attachments. Cybercriminals use ‘Social Engineering’ techniques to trick users into opening attachments or clicking on links that lead to infected websites.
- Always turn on email protection of your antivirus software
Limit access to those that need it:
- To minimize the potential impact of a successful ransomware attack against your organization, ensure that users only have access to the information and resources required to execute their jobs. Taking this step significantly reduces the possibility of a ransomware attack moving laterally throughout your network. Addressing a ransomware attack on one user system may be a hassle, but the implications of a network-wide attack are dramatically greater.
Train the Employees:
- Educate employees to recognize potential threats. The most common infection methods used in ransomware campaigns are still spam and phishing emails. Quite often, user awareness can prevent an attack before it occurs. Take the time to educate your users, and ensure that if they see something unusual, they report it to your security teams immediately.
