The regular boot sequence of a typical Qualcomm Snapdragon chipset-powered Android device is initiated with the Primary Bootloader (PBL), although there exists an alternative boot mode called Emergency Download Mode (EDL). The latter is strictly intended for OEM servicing and can be used to ‘unbrick’ a device with appropriate software binaries via a protocol named ‘Firehose’. Interestingly, EDL is often utilized by tinkerers to get low-level partition access, which can further be exploited to achieve bootloader unlock on some devices. Based on this principle as well as the previous research work done by the Aleph Security team, XDA Senior Member alexenferman has now discovered a generic method to unlock the bootloader of a bunch of ZTE phones without any data loss.
ZTE apparently uses the ‘devinfo’ partition to store crucial bootloader state parameters, including the lock/unlock status. As the Firehose protocol has a provision of reading the contents of individual partitions, one can dump the ‘devinfo’ partition from a bootloader-locked device, change the offset where the unlocking parameters are stored, and write the modified image back to the device to unlock the bootloader. Unlike Xiaomi and some other OEMs, ZTE doesn’t even put a safeguard before the EDL mode against such ‘attacks’, thus you can easily trigger the device to boot to emergency download mode via a simple ADB command. The only catch is that the method won’t work on ZTE phones that launched with Android 8.0 Oreo or newer, and it also won’t work on flagship devices like the Axon 9 Pro, Axon 10 Pro, Axon M, etc.
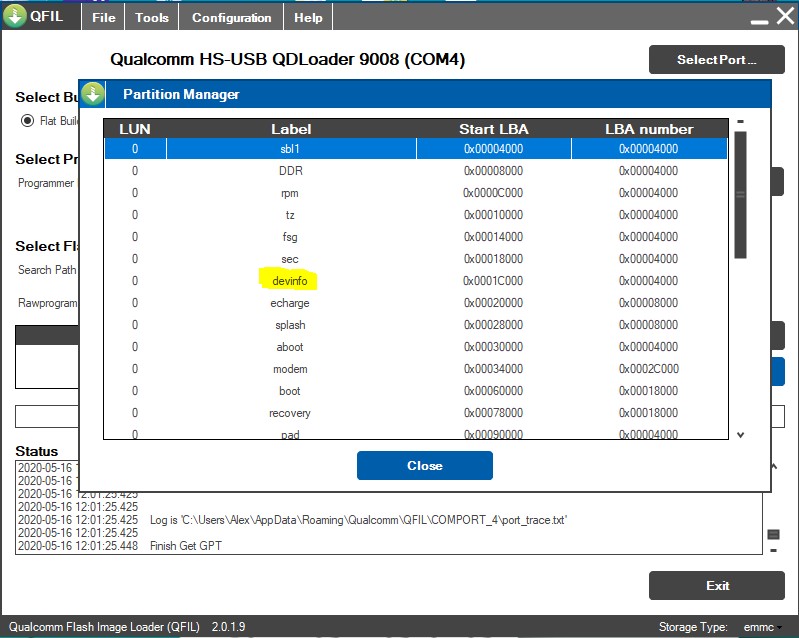
Dumping the ‘devinfo’ partition using QFIL
According to XDA Recognized Developer deadman96385, this method works with the following devices:
Devices with MSM8909 (Qualcomm Snapdragon 210) SoC
- ZTE Avid 4 (Z855) (code-name: calbee)
- ZTE Maven 2 (Z831) (code-name: chapel)
- ZTE Maven 3 (Z835) (code-name: draco)
- ZTE Majesty Pro Plus (Z899VL) (code-name: elden)
- Unknown ZTE (code-name: forbes)
- ZTE ZMAX One (Z719DL) (code-name: gemi)
- ZTE Tempo X (N9137) (code-name: grayjoylite)
- ZTE Grand X View 2 (K81) (code-name: helen)
- ZTE Overture 3 (Z851) (code-name: jeff)
- ZTE Fanfare 3 (Z852) (code-name: kelly)
- ZTE ZFive G LTE (Z557BL) (code-name: lewis)
- ZTE ZFive C (Z558VL) (code-name: loft)
- Unknown ZTE (code-name: refuge)
- ZTE N818S (code-name: sapphire/sapphire4G)
- ZTE Blade Vantage (Z839) (code-name: sweet)
Devices with MSM8952 (Qualcomm Snapdragon 617) SoC
- Android 5.1.1
- ZTE Grand X Max 2 (Z988) (code-name: jerry)
- ZTE Imperial Max (Z963U) (code-name: lily)
- ZTE Max Duo LTE (Z963VL) (code-name: nancy)
- ZTE Axon Max (C2016) (code-name: orchid)
- ZTE Max Duo LTE (Z962BL) (code-name: tom)
- Android 6.0.1
- ZTE ZPAD (K90U) (code-name: gevjon)
- ZTE AT&T Trek 2 (K88) (code-name: jasmine)
- ZTE Grand X Max 2 (Z988) (code-name: jerry)
- ZTE Axon Max (C2016) (code-name: orchid)
- ZTE ZMAX Pro (Z981) (code-name: urd)
- Android 7.1.1
- ZTE AT&T Trek 2 (K88) (code-name: jasmine)
- ZTE Axon 7 Mini (B2017G) (code-name: tulip)
Devices with MSM8920/MSM8937/MSM8940/MSM8953 (Qualcomm Snapdragon 427/430/435/625) SoCs
- ZTE Blade Force/ZTE Warp 8 (N9517) (code-name: warp8)
- ZTE Grand X4 (Z956/Z957) (code-name: finacier)
- ZTE Blade Spark (Z971) (code-name: peony)
- ZTE Blade X (Z965) (code-name: proline)
- ZTE Max XL/ZTE Bolton (N9560) (code-name: bolton)
- ZTE Blade Z Max (Z982) (code-name: crocus)
- Unknown ZTE (code-name: flame)
- ZTE Blade X Max (Z983) (code-name: stollen)
- ZTE Blade Max View (Z610DL) (code-name: violet)
- ZTE Max Blue LTE (Z986DL) (code-name: florist)
- ZTE AT&T Primtime (K92) (code-name: primerose)
Additionally, the ZTE Avid 4, ZTE Tempo X, ZTE Imperial Max, and ZTE Grand X View 2 should also be compatible with this procedure. Interested users should take a look at deadman96385‘s unofficial ZTE Firehose repo and pick the right set of programmers before fiddling with their devices. The step-by-step bootloader unlocking process can be found in the thread linked below.
Bootloader Unlocking on Qualcomm ZTE Devices — XDA Discussion Thread
The post Dozens of old ZTE phones with Qualcomm processors can now be bootloader unlocked appeared first on xda-developers.
