 Researchers at Check Point Research (CPR) on Wednesday said they recently discovered a new and innovative malicious malware on the Google Play Store which spreads itself via mobile users’ WhatsApp conversations and can also send further malicious content via automated replies to incoming WhatsApp messages.
Researchers at Check Point Research (CPR) on Wednesday said they recently discovered a new and innovative malicious malware on the Google Play Store which spreads itself via mobile users’ WhatsApp conversations and can also send further malicious content via automated replies to incoming WhatsApp messages.
This unique method enables threat actors to distribute phishing attacks, spread false information or steal credentials and data from users’ WhatsApp accounts, and more.
Called ‘FlixOnline’, the app is a fake service that claims to allow users to view Netflix content from all around the world on their mobiles for free. However, instead of allowing the mobile user to view Netflix content, the app monitors the user’s WhatsApp notifications and sends automatic replies to incoming messages using content that it receives from a remote command and control (C&C) server.
The malware sends the following response to its victims, luring them with the offer of a free Netflix service:
“2 Months of Netflix Premium Free at no cost For REASON OF QUARANTINE (CORONA VIRUS)* Get 2 Months of Netflix Premium Free anywhere in the world for 60 days. Get it now HERE https://bit[.]ly/3bDmzUw.”
Utilizing this technique, a threat actor could perform a wide range of malicious activities:
- Spread further malware via malicious links
- Stealing data from users’ WhatsApp accounts
- Spreading fake or malicious messages to users’ WhatsApp contacts and groups (for example, work-related groups)
- Extort users by threatening to send sensitive WhatsApp data or conversations to all of their contacts
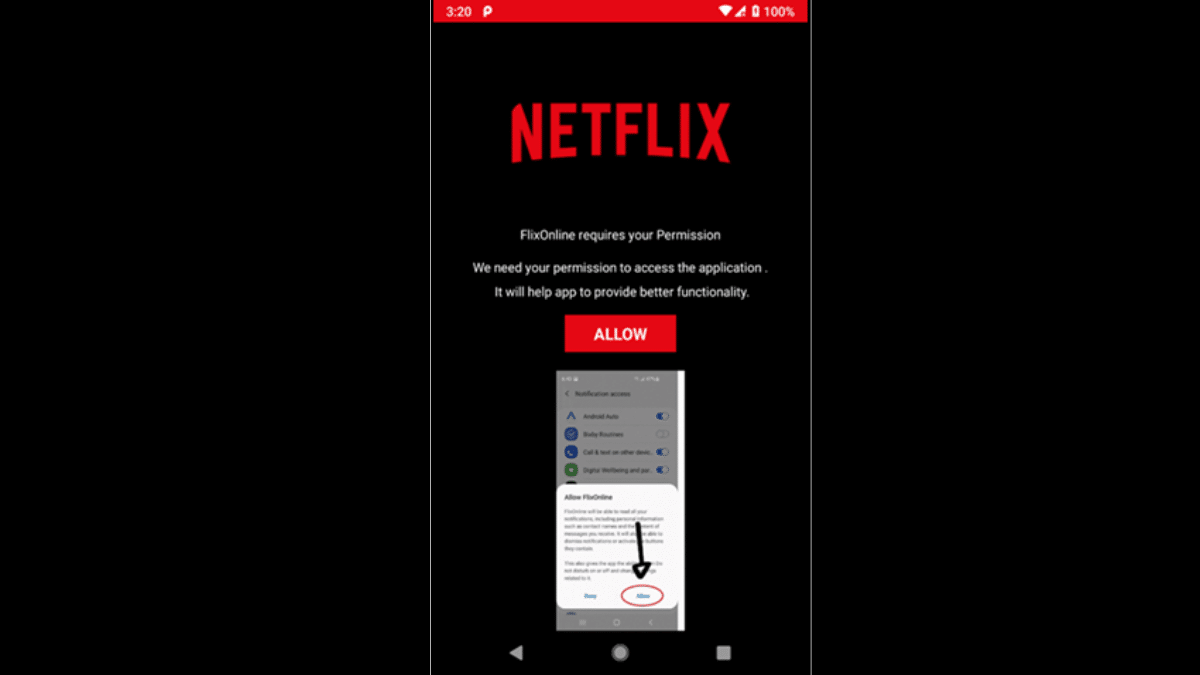
When the application is downloaded from the Play Store and installed, the malware starts a service that requests ‘Overlay’, ‘Battery Optimization Ignore’, and ‘Notification’ permissions. The purpose behind obtaining these permissions is:
- Overlay allows a malicious application to create new windows on top of other applications. This is usually requested by malware to create a fake “Login” screen for other apps, with the aim of stealing victim’s credentials.
- Ignore Battery Optimizations stops the malware from being shut down by the device’s battery optimization routine, even after it is idle for an extended period.
- The most prominent permission is the Notification access, more specifically, the Notification Listener service. Once enabled, this permission provides the malware with access to all notifications related to messages sent to the device, and the ability to automatically perform designated actions such as “dismiss” and “reply” to messages received on the device.
If the permissions are granted, the malware has everything it needs to start distributing its malicious payloads and send out auto-generated replies to incoming WhatsApp messages using the payload received from the C&C server.
“This ‘wormable’ Android malware features innovative and dangerous new techniques for spreading itself, and for manipulating or stealing data from trusted applications such as WhatsApp,” the cybersecurity researchers wrote in a blog post.
“It highlights that users should be wary of download links or attachments that they receive via WhatsApp or other messaging apps, even when they appear to come from trusted contacts or messaging groups,” they warned.
Following the discovery of the malware, Check Point Research notified Google about the malicious application and the details of its research. Google quickly removed the application from the Play Store. Over the course of 2 months, the “FlixOnline” app was downloaded approximately 500 times.
Check Point Researchers have advised the users who are affected by the malware to remove the application from their device and change their passwords.
The post Fake Netflix App On Google Play Store Spreads Malware Via WhatsApp appeared first on TechWorm.
