
If you’ve been reading about security bugs online, you’ve probably ran into scores given to exploits. These are scored based on the Common Vulnerability Scoring System, used to categorize exploits into the Common Vulnerability and Exposures database. We’ll discuss what makes up the score.
What Affects the Score?
The total base score is ranked 0 to 10, and is composed of three subscores—exploitability, impact, and scope. A lower exploitability score is worse, as is a higher impact score. An exploit that can be easily exploited over the network by anyone and has a high impact would be critical, and an exploit that requires physical access or user interaction and doesn’t do much would be very low impact.
Exploitability refers to how easily a vulnerability can be exploited by an attacker. The fewer things that are required from the attacker, the easier it is to exploit. There are four components to this:
- Attack Vector is what network relation the attacker must have to the source to pull off the exploit. The easiest and most severe is Network, which means the exploit can be pulled off by anyone with public access. Adjacent means the attacker must be on a shared network, and local means local network. Physical requires direct interaction and often user interaction.
- Attack Complexity refers to a bit more than just how complicated it is. Higher attack complexity means more pieces must be in the right places to exploit the vulnerability. Low complexity means the exploit can be exploited on a wide range of systems.
- Privileges Required. None means it can be exploited by anyone on the web,
Low means the attacker has some sort of authorization, and High means the user must have extended privileges to exploit it. - User Interaction, whether or not the target must do something for the exploit to work. This metric is binary, either interaction is required or not.

Impact refers to how severe the exploit is, and how much it affects the target system. This has three components:
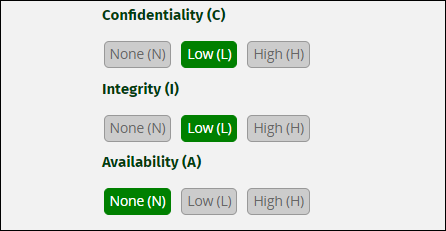
- Confidentiality, or unauthorized reads (i.e., whether or not the attack gives access to resources that are supposed to be privat). Low is a basic exposure of some private info, and High means that serious data (often customer data) could be exposed.
- Integrity, or unauthorized writes. Low refers to the attacker being able to write to specific files, and High gives the attacker write access to anything within the target’s scope.
- Availability refers to whether or not the exploit can cause an application to go down, including but not limited to DDoS attack vectors. Low means parts of the application can go offline, and High means most of or the entire application can be brought down using the exploit. This is different. Confidentiality and Integrity refer to the data used by the application, and Availability refers to the operation of the service itself. There are scenarios where this can overlap with Integrity—an exploit giving attackers full write access to the system can also give them the ability to delete the application itself.
Lastly, Scope. This one is a bit more complicated, but it basically refers to whether or not the exploit gives access to resources outside of the control of the target, usually outside of a security sandbox or barrier. The CVSS guide defines it as “when a security boundary mechanism separating components is circumvented due to a vulnerability and this causes a security impact outside of the security scope of the vulnerable component.”
Examples of this include a vulnerability in a virtual machine allowing writes on the host, vulnerabilities in microprocessors giving access to other threads, cross-site scripting or URL redirection attacks that can give access to a users browser, and sandbox escape).
Ultimately, this all comes down to a single score, and a description like “High” or “Critical” describing the overall severity.

Alongside the score, you’ll often see the vector string, which looks confusing at first but is really just abbreviated key-value pairs for each component.
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:L/A:N
You can actually take any vector string, and load it into the calculator after the hashtag to get a better view of it:
https://www.first.org/cvss/calculator/3.1#CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:L/A:N
The other main score is the Temporal Score, which tracks how an exploit’s severity changes over time. This includes code maturity (if the exploit is being used in practice), whether or not there are any kind of fixes, and how confident the publisher is about the details of the exploit.

