Microsoft revealed plans to integrate DNS over HTTPS in Windows 10 in November 2019. DNS over HTTPS encrypts DNS lookups to improve privacy, security and reliability of the connection.
Most devices that are connected to the Internet rely on plain text DNS lookups. These lookups “translate” domain names, e.g. ghacks.net, to IP addresses that devices use to establish connections. Anyone listening on the network, including the ISP, knows exactly which sites and services are opened on the device because of this.
Browser makers such as Mozilla, Google, and Opera announced support for DNS over HTTPS and have started to integrate the feature into browsers. The solutions would allow users of these browsers to make use of the feature but it would only apply to the browser.
Microsoft’s plan to introduce support for DNS over HTTPS in the operating system would enable support for all programs (including browsers) on that system.
The company decided to enable or disable the functionality based on the selected provider. If the DNS provider supports DNS over HTTPS, it would be used and otherwise, it would not. In other words: many users will see the privacy and security of DNS lookups improved once the feature lands in Windows without even noticing that this happened.
Microsoft has integrated DNS over HTTPs in recent Insider versions of Windows 10. Note that the feature has not yet been implemented in stable versions of Windows 10. It is not clear when this will be the case as Microsoft provides no schedule for that.
Note: The build number needs to be at least 19628. You can check the build number by loading winver from the Start menu.
How to enable DNS over HTTPS on Windows 10
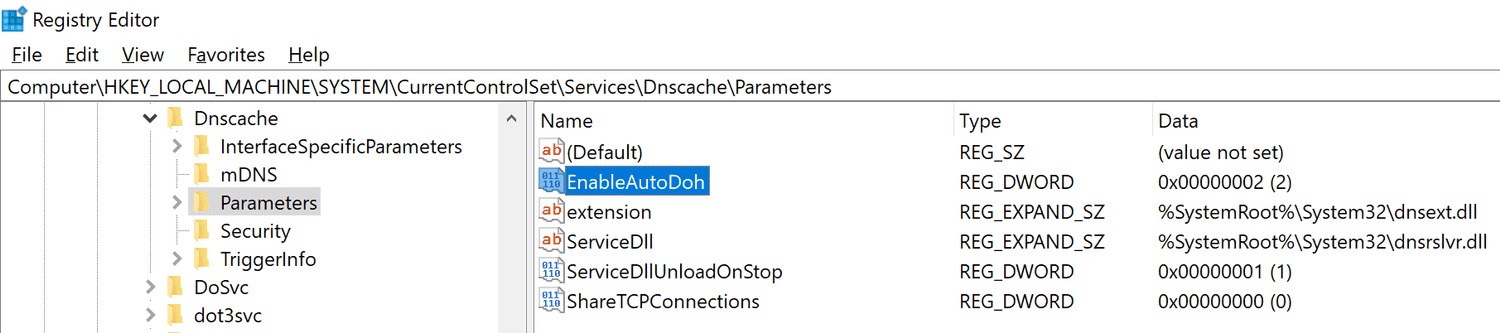
Only Insider builds require that DNS over HTTPS is enabled in the Registry. Microsoft notes that this won’t be necessary once the feature lands in stable versions of Windows 10.
- Tap on Start.
- Type regedit.exe and hit Enter to load the Registry Editor.
- Confirm the UAC prompt if it is displayed.
- Go to HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesDnscacheParameters.
- Right-click on Parameters and select New > Dword (32-bit) Value.
- Name it EnableAutoDOH.
- Set its value to 2.
- Restart the Windows system.
You need to make sure that a provider that supports DNS over HTTPS is selected. Microsoft highlights three providers on its Tech Community website:
| Server Owner | Server IP addresses |
| Cloudflare | 1.1.1.1
1.0.0.1 2606:4700:4700::1111 2606:4700:4700::1001 |
| 8.8.8.8
8.8.4.4 2001:4860:4860::8888 2001:4860:4860::8844 |
|
| Quad9 | 9.9.9.9
149.112.112.112 2620:fe::fe 2620:fe::fe:9 |
These servers need to be set as the DNS server addresses on the system as these are the servers that get auto-promoted.
Administrators may add other DNS over HTTPS capable servers to the system so that these may be used as well.
The following commands need to be run with elevated privileges to add DNS over HTTPS capable servers to the system:
- netsh dns add encryption server=<your-server’s-IP-address> dohtemplate=<your-server’s-DoH-URI-template>
To verify the template, run the following command:
- netsh dns show encryption server=<your-server’s-IP-address>
Here is how you change DNS settings:
- Select Start > Settings > Network & Internet > Change adapter settings.
- Right-click on the adapter that is used and select Properties.
- Double-click on either Internet Protocol Version 4 or 6 (or both one after the other) to set a new DNS provider.
- Select “Use the following DNS server addresses”.
- Enter the addresses listed above.
- Click ok to apply the changes.
Note that you can revert the changes at any time by switching to the “automatically” option or editing DNS servers.
How to test DNS over HTTPS on Windows 10
Windows 10 comes with built-in functionality to test whether DNS over HTTPS is working.
- Open a PowerShell window.
- Run the following commands one after the other:
- pktmon filter remove // removes any existing filters.
- pktmon filter add -p 53 // adds traffic filter for port 53, the port that classic DNS uses.
- pktmon start –etw -m real-time // start real-time logging of traffic.
- If DNS over HTTPS is used, it show “little to no traffic”.
Now You: What is your take on DNS over HTTPS? Will you use it?
