
Apache is one of the most popular web servers but its default configuration contains questionable choices on many Linux distributions. Apache tends to advertise its specific version and the platform it’s running on, information that could be valuable to attackers.
This quick article will show you how to disable this output to help protect your server. There’s usually no reason for it to be active and turning it off should only take a minute.
What’s the Problem?
Here’s a fresh Apache 2.4 installation displaying a directory index:
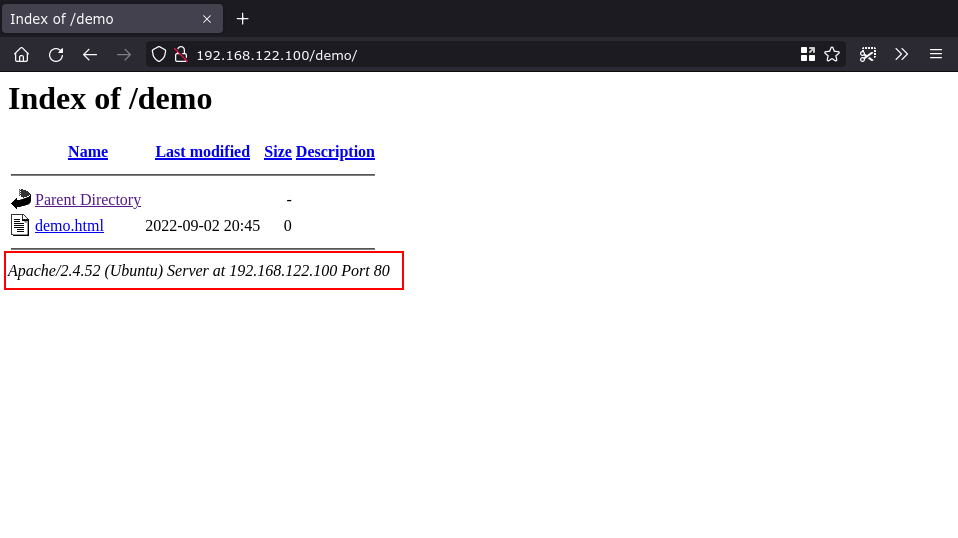
The page’s footer reveals the Apache version code, operating system name, and internal IP address and port number of your server.
These are potentially sensitive details. A zero-day vulnerability in Apache might affect only a small range of versions. By leaving this output turned on, you’re displaying to the world whether your machine’s at risk. This makes it much easier for attackers to identify your host as a potential target.
Apache refers to this data as its “server signature.” It’s not confined to the directory index pages: the version code gets included in every HTTP response within the Server header:
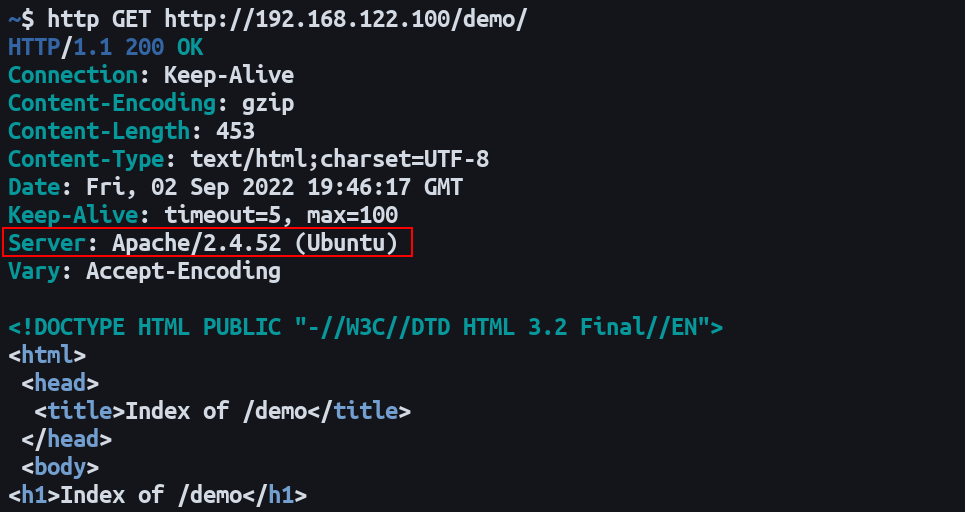
It’ll be present irrespective of the response’s status code. Attackers can find your precise Apache version by simply pinging a request to your server, irrespective of whether they know a valid URL.
Disabling the Server Signature
There are two parts to disabling this unwanted output. First is the ServerSignature value in your Apache config file. The location of this file varies; /etc/apache2/apache2.conf and /usr/local/apache2/conf/httpd.conf are two common possibilities. The ServerSignature directive’s also supported inside .htaccess files in your web root.
Set the directive to Off to disable the signature that appears on server-generated webpages:
ServerSignature Off
Restart Apache to apply the change:
$ sudo service apache2 restart

This affects directory listings, Apache’s default error pages, and other HTML output produced by the server. Off completely removes the signature line. The setting optionally supports a third value, EMail, that provides a link to send an email to the address defined by ServerAdmin:
ServerAdmin [email protected] ServerSignature EMail
This replaces the Apache version information with the email link.
Managing Server Tokens
The content of the Server response header is controlled by a different setting, ServerTokens. This can only be set by your server’s global configuration file. It’s not supported inside .htaccess files.
The default value is Full which presents the precise version string and operating system name observed in the example above. This can also include the version numbers of loaded modules and CGI content engines such as PHP.
The following alternative values are supported:
Full–Apache/2.4.2 (Ubuntu)Prod–ApacheMajor–Apache/2Minor–Apache/2.4Min–Apache/2.4.2OS– Same asFullbut without information about loaded modules
The Prod choice is the safest value. You can think of it as Production, although it’s actually short for ProductOnly. This server token means the Server header will only reveal you’re using Apache, without any extra info about the release. Attackers will have to do more trial and error investigation to find exploitable vulnerabilities in your installation.
Unfortunately there’s no way to remove the Server header altogether. Apache actually maintains that disabling it “does nothing at all to make your server more secure” and suggests use of Min to make it easier to debug interoperational problems.
However most people never consume the Server header and it’s always safest to advertise the least possible information about your system. While it won’t prevent the exploit of vulnerabilities, ServerTokens Prod could deter attackers from making speculative attempts. It’ll also make it harder for passersby to glean details of your tech stack’s inner workings. It’s only a small hardening but one day it could be the difference you need.
What About PHP?
Apache’s often used in front of websites and applications powered by PHP. Unfortunately PHP has its own habit of providing its version number to the internet. It will appear in the X-Powered-By header of responses sent by your PHP code.
You can turn this off by modifying your PHP configuration file with the following line:
expose_php = Off
The config file can usually be found at /etc/php/8.1/apache2/php.ini. Replace 8.1 with the PHP version you’re using. You’ll need to restart your web server to apply the change.
Summary
Apache’s default configuration exposes the precise version number of your server, as well as its operating system and IP address. This seemingly innocuous information can lend a helping hand to attackers looking for vulnerable servers.
Turning off the server signature is a quick way to harden your environment. It’s also a good idea to address similar information exposure from other software in your stack at the same time. PHP and some web frameworks come with similar vulnerabilities.
