
In a report this week, Microsoft said that it disrupted operations of a nation-state threat group that was using its Azure cloud infrastructure for cyber attacks.
Microsoft refers to the actor by the name Gadolinium and says that it’s been active for about a decade targeting organizations in the maritime and health industry; more recently, the hackers expanded focus to higher education and regional government entities.
Abusing cloud services
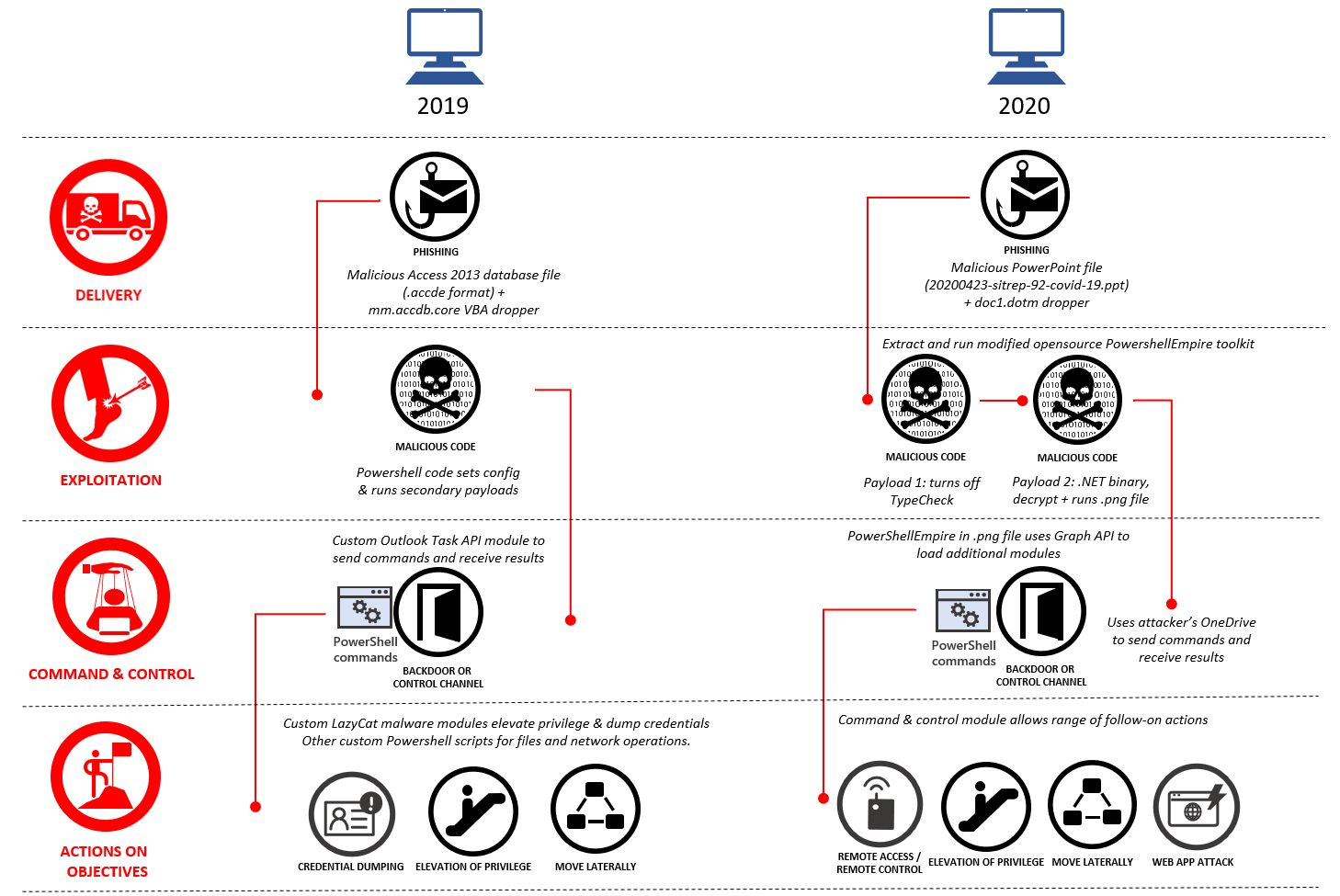
Based on detections of various components serving Gadolinium’s malicious activity, Microsoft Threat Intelligence Center (MSTIC) identified 18 Azure Active Directory applications the group used for their command and control infrastructure.
These were part of the actor’s custom version of the PowerShell Empire post-exploitation toolkit that enabled them to deploy malicious modules on a compromised computer using Microsoft Graph API calls.
“It provides a command and control module that uses the attacker’s Microsoft OneDrive account to execute commands and retrieve results between attacker and victim systems” – Microsoft
Earlier this year, in April, the company removed the 18 Azure Active Directory applications, thus disrupting, even if temporarily, the malicious Gadolinium activity.
Attacks from this threat group start with spear phishing emails to deliver malicious documents (PowerPoint in 2020) that drop a file typically with two payloads.
The attack chain continues with extracting and deploying the modified version of PowerShell Empire disguised as a PNG image file. This enables the attacker to download more modules on the compromised computer and establish a backdoor channel.
The role of the Azure Active Directory application was to set up the victim systems so it could receive commands from and exfiltrate data to a OneDrive storage account controlled by the attacker.
This configuration made it particularly difficult to detect malicious activity at the network level because of the legitimate tools and services involved, Microsoft says in a report on Thursday.
While Microsoft does not provide many details about Gadolinium apart from its longevity and targets of interest, the Fraunhofer FKIE research institute lists it under other aliases from various cybersecurity companies: APT40, BRONZE MOHAWK, Gadolinium, Kryptonite Panda.
Past reports from FireEye referred to the group as APT40, TEMP.Periscope, and TEMP.Jumper, suspecting it to be a Chinese cyber espionage threat actor. In research published in March 2018, the company says cybersecurity firm Proofpoint tracks this cyber espionage actor as Leviathan.
