Most people view the internet as a powerful tool for accessing information in an instant, but advertising companies see it in just the same way — often utilizing the very internet connection you depend on for said information to track your every move and report back with personally identifiable statistics.
A firewall can help preserve your anonymity and privacy over the internet by giving you the distinct choice to allow or deny these connection requests. That’s just one reason why a newly released jailbreak tweak dubbed NetFence by iOS developer FoxfortMobile might be of interest to you.
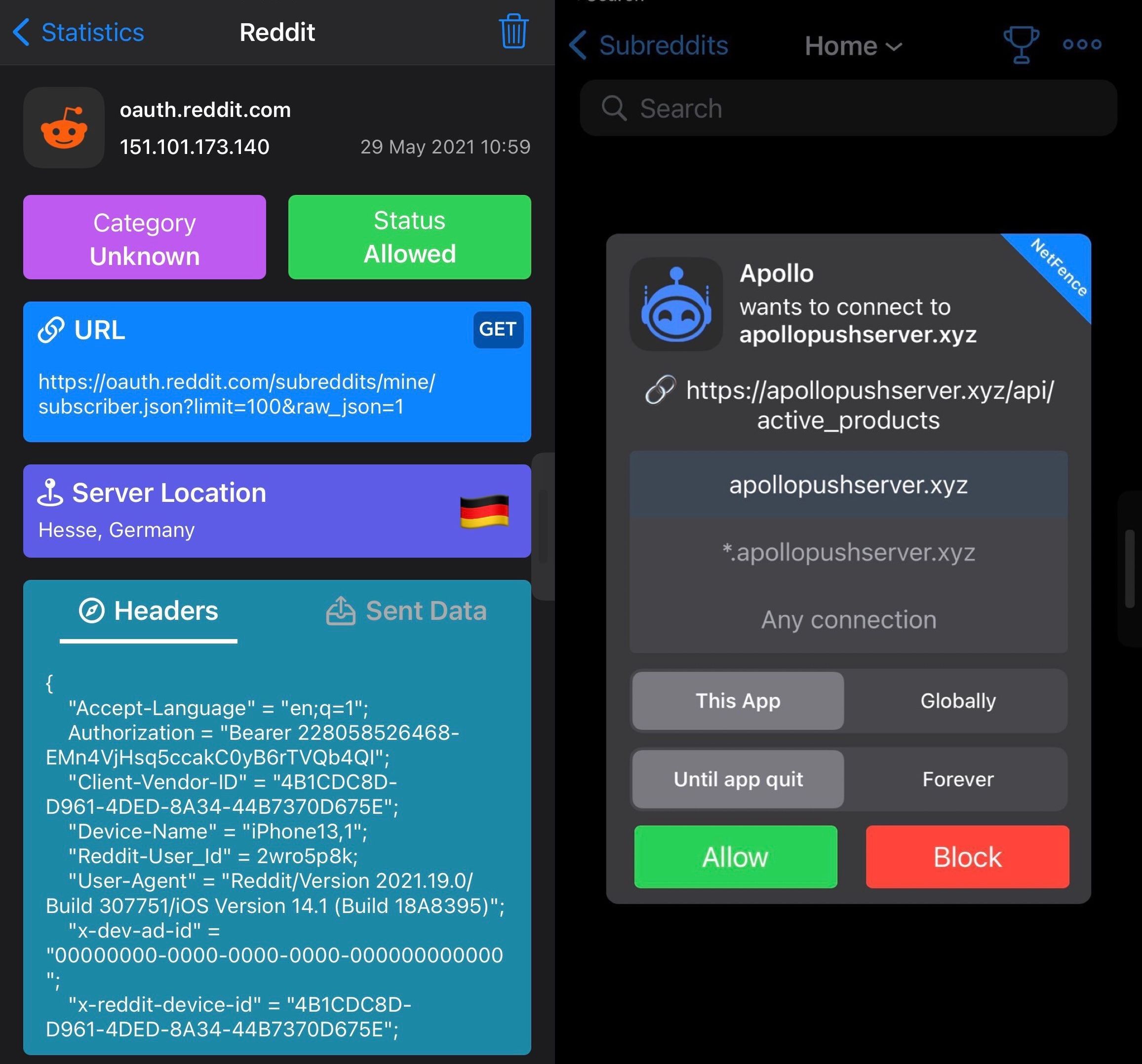
To put it briefly, NetFence is a network monitoring utility that intercepts the outgoing network connections on your jailbroken iPhone or iPad. With it, you can be more informed about the types of network requests that apps and services are making and have the option to either allow or deny those connections with a tap.
NetFence keeps running records of all the data leaving your device and notes the servers that it’s going to. With this powerful utility, users will have a better idea of the types of data being collected about them and where it’s going. As a bonus, NetFence can alert you to known ads and tracking hosts that might be collecting information about you:
One of the things we like about NetFence is the firewall-like functionality in which a pop-up is shown with information about outgoing information on your device. You can then choose to allow or deny that connection via one of the integrated buttons. The sheer volume of these pop-ups might overwhelm some users, which is why the developer created a Silent Mode feature. It reduces the number of pop-ups while continuing to monitor in the background.
Some of the things you can do with NetFence include:
- View real-time network requests being made by each individual app (even if they’re running in the background)
- Allow or deny specific connections for individual apps at runtime
- Allow or deny requests either permanently or temporarily
- Allow or deny connections to subdomains of a host, even with wildcard syntax rules
- View real-time network requests being made by web browsers (Safari and web views from other apps)
- Use Silent Mode to record network traffic in the background without being pestered by prompts
- Global rules to allow or block host matching in any enabled app
- Hide requests that are made by the operating system itself
- View network requests and statistics as comprehensive graphs or detailed lists
- Examine the types of information being recorded in network requests
- Search for specific requests made by a host or app
- Export requests to a text file
- Export setup rules to text for use in third-party network blocker software
- View organizations for which unmapped IP addresses belong to
- And much more…
As noted by the developer, NetFence can be used as an ad-blocker, but it wasn’t originally designed to be used as one. It’s also worth noting that NetFence doesn’t install any profiles on your device, nor does it depend on a VPN like many of the firewall apps in the App Store. NetFence instead runs natively on your jailbroken device. Users can still continue to use VPN software alongside NetFence if they would like.
NetFence does add a preference pane to the Settings app post-installation, but the only thing you’ll do there is activate your license after downloading. Once that’s done, it will provide a link to the app, which gets added to the Home Screen:
If you’d like to take control over your handset’s outgoing network requests then you can purchase the new NetFence add-on from the Packix repository for $3.99. NetFence supports all jailbroken iOS 13 & 14 devices, and will be a useful utility whether you’re interested in simply learning more about the network requests being made on your device or you simply want to block certain requests from happening.
Do you plan to take advantage of NetFence? Discuss why or why not in the comments section down below.
