If you have heard of ZeroLogon but not sure if your server has been patched up for this vulnerability, here is a PowerShell script that you can use to validate the CVE 2020-1472 patch.
Requirement
If you run the script on a desktop computer, make sure WinRM is enabled in all domain controllers.
If you run the script on one of the domain controllers, make sure WinRM is enabled between all domain controllers.
You will also need appropriate permissions to query the data.
- If child domains are present: Enterprise admin
- If single forest, single domain: Domain admin
Usage
The script will recursively query all the domain controllers within the Forest, using WMI to retrieve the DC Name, OS and installed KB and save the result to a folder called CISA on the current user’s desktop.
Download the script and run it, in an elevated PowerShell console on the domain controller. You can also copy the entire code and paste it in the PowerShell ISE window and run it.
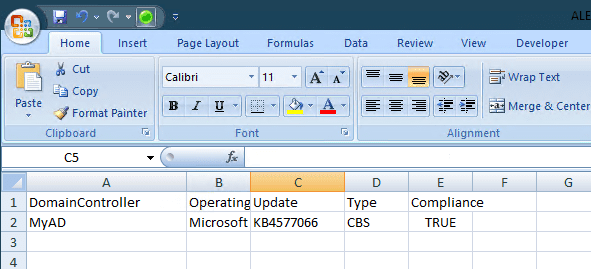
Then open the Alert.csv file saved in the %userprofile%CISA<date> folder.
If you see a TRUE in Compliance column, you have been patched.
The post Script to Validate Your Active Directory Controller is Patched for ZeroLogon appeared first on Next of Windows.
