
To stay safe online, everyone needs to recognize malicious attachments that are commonly used in phishing emails to distribute malware.
When distributing malware, threat actors create spam campaigns that pretend to be invoices, invites, payment information, shipping information, eFaxes, voicemails, and more. Included in these emails are malicious Word and Excel attachments, or links to them, that when opened and macros are enabled, will install malware on a computer.
Before Word or Excel executes macros in a document, though, Office requires you to click on the ‘Enable Editing’ or ‘Enable Content’ buttons, which you should never do.
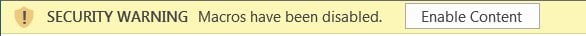
To trick users into clicking these buttons, the malware distributors create Word and Excel documents that contain text and images stating that there is an issue displaying the document. It then prompts recipients to click ‘Enable Content’ or ‘Enable Editing’ to see the contents correctly.
The combination of text and images in these malicious attachments are called ‘document templates.’
Below are different document templates that have been used in the spam campaigns for some of the more wide-spread malware infections.
It should be noted that these document templates can also be used with different malware than what is associated below. Furthermore, this is a sample of the more common templates, but many others are out there.
BazarLoader
BazarLoader is an enterprise-targeting malware developed by the same group behind the TrickBot trojan. When installed, threat actors use BazarLoader/BazarBackdoor to remotely access your computer, which is then used to compromise the rest of your network.
When a network has been infected with BazarLoader, it is common for the threat actors to ultimately deploy the Ryuk ransomware to encrypt all the devices on a network.
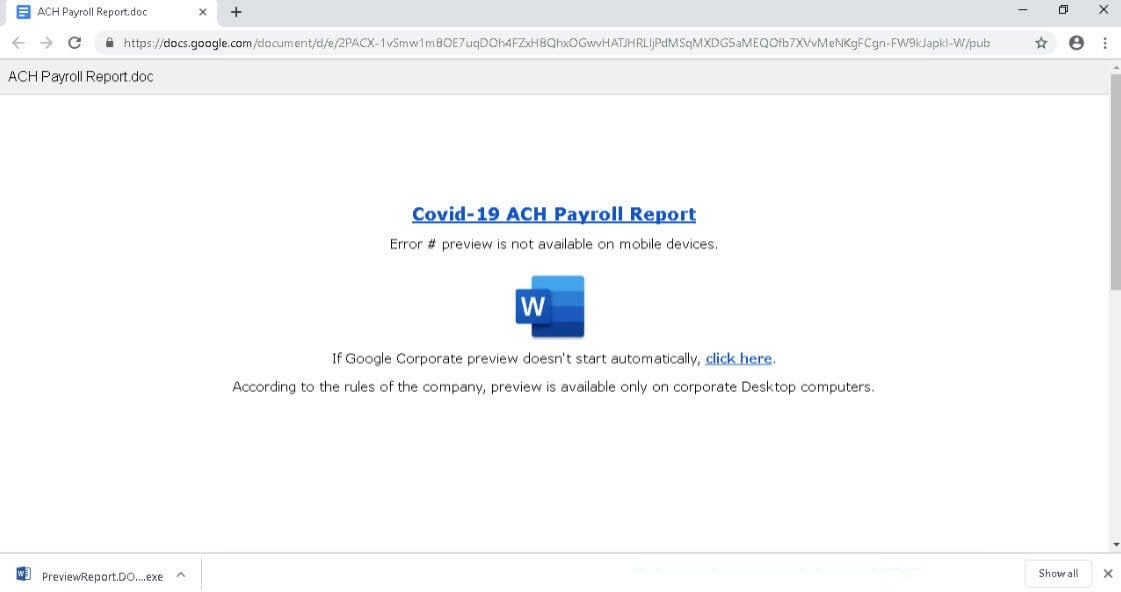
Phishing emails that distribute BazarBackdoor via phishing emails usually contain links to alleged Word or Excel documents hosted on Google Docs and Google Sheets.
These Google Docs documents, though, pretend to have a problem and prompt you to download the document. This download is actually an executable that installs BazarLoader, as shown below.
Dridex
Dridex is an advanced and modular banking Trojan first spotted in 2014 and is continuously updated.
When infected, Dridex will download different modules that can be used to steal passwords, provide remote access to a computer, or perform other malicious activities.
When Dridex compromises networks, it commonly leads to the deployment of BitPaymer or Dridex ransomware attacks.
Another ransomware known as WastedLocker is also believed to be tied to Dridex, but one cybersecurity firm does not agree with these assessments.
Unlike other malware distribution campaigns, the Dridex gang tends to use more stylized document templates that show small or obfuscated content and prompt you to click Enable Content to see it better.
For example, the template below states that the document was created in an earlier version of Microsoft Office Word, and displays a hard-to-read document below it.
Dridex also uses more stylized document templates pretending to be shipping information for DHL and UPS.
Finally, Dridex will show small hard-to-read payment invoices that prompt you to click ‘Enable Editing’ to view it correctly.
As you can see from the examples above, Dridex likes to use images of embedded documents with company logos and letterhead to trick users into enabling macros.
Emotet
Emotet is the most widely distributed malware through spam emails containing malicious Word or Excel documents. Once infected, Emotet will steal a victim’s email and use the infected PC to spew out further spam to recipients worldwide.
Users infected with Emotet will eventually be further infected with trojans such as TrickBot and QakBot. Both of these Trojans are used to steal passwords, cookies, files, and lead to an organization’s network-wide compromise.
Ultimately, if infected with TrickBot, a network will likely become affected by a Ryuk or Conti ransomware attack. For those affected by QakBot, they may be hit by the ProLock ransomware.
Unlike Dridex, Emotet does not use images of actual documents in their document templates. Instead, they utilize a wide range of templates that show a warning box that the document can’t be viewed correctly and that users need to click on ‘Enable Content’ to read it.
For example, the ‘Red Dawn‘ template shown below states that “This document is protected,” and then prompt you to Enable Content to read it.
This next template pretends that it could not be opened correctly as it was created on an ‘iOS device.’
Another states that the document was created on ‘Windows 10 Mobile,” which is a strange message as Windows 10 Mobile has been discontinued for some time.
The next template pretends that the document is in ‘Protected View,’ and a user needs to click ‘Enable Editing’ to see it properly.
The next template is a bit more interesting as it tells users to accept Microsoft’s license agreement before they can view the document.
Another interesting template pretends to be a Microsoft Office Activation Wizard, which prompts users to ‘Enable Editing’ to finish activating Office.
Finally, Emotet is known to use a document template that pretends to be a Microsoft Office Transformation Wizard.
As you can see, instead of stylized document templates, Emotet uses general warnings to try and convince users to enable macros in an attachment.
QakBot
QakBot, or QBot, is a banking trojan that spreads via phishing campaigns that deliver malicious Microsoft Word documents, usually to businesses.
QakBot is a modular Trojan that includes the ability to steal banking information, install other malware, or provide remote access to an infected machine.
Like other trojans in this article, QakBot has also partnered with a ransomware infection called ProLock that is usually the final payload of an attack.
Compared to Emotet, QakBot campaigns tend to utilize more stylized document templates. The most common template used by QakBot spam campaigns pretends to be from DocuSign, as shown below.
Other templates include ones pretending to be from Microsoft Defender or a Word update and activation screen, like the one below.
All executable attachments
Finally, you should never open attachments that end with the .vbs, .js, .exe, .ps1, .jar, .bat, .com, or .scr extensions as they can all be used to execute commands on a computer.
As most email services, including Office and Gmail, block “executable” attachments, malware distributors will send them in password-protected archives and include the password in the email.
This technique allows the executable attachment to bypass email security gateways and reach the intended recipient.
Unfortunately, Microsoft decided to hide file extensions by default, which allow threat actors to trick users into running unsafe files. Due to this, BleepingComputer strongly recommends that all Windows users enable the display of file extensions.
If you receive an email containing one of these executable file types, it is almost undoubtedly malicious and should be immediately deleted.
