
If you use two-factor authentication (also known as 2FA) on your online accounts, you may want to switch to a hardware security key instead.
When 2FA is enabled and you attempt to log into your account, like Twitter, a temporary code will be sent to your phone. You need to enter this code to sign in to your account. Since only you should have access to your phone/code (one factor) and your login credentials (the second factor), two factor essentially verifies your identity and ensures only you are logging into your account.
There are downsides to two-factor authentication. If you lose your phone, or if it’s breached by a hacker who’s swapped your SIM or somehow gained access to your device, they’ll obviously be able to retrieve your code and potentially use it to hack into your account (especially if they also know your login credentials). Luckily, a security key can help you avoid this nightmare.

What is a hardware security key?
Hardware security keys (also called security keys, U2F keys, or physical security keys) add an extra layer of security to your online accounts. They protect against automated bots and targeted attacks by leveraging cryptography to verify your identity and the URL of a login page. They’re therefore phishing-resistant, too, as they can ascertain whether you’re trying to log into a legit service.
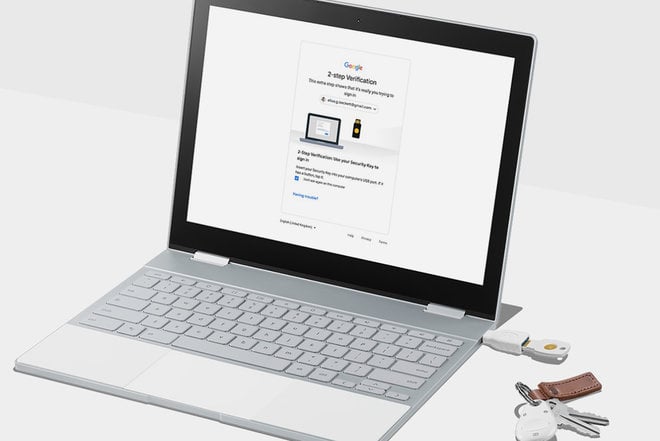
Security keys connect to your device via USB-A, USB-C, Lightning, NFC, and Bluetooth, and they’re portable enough to be carried on a keychain. Most of them use an open authentication standard, called FIDO U2F (or the improved FIDO2 standard), and some even feature hardware that’s designed to resist physical attacks aimed at extracting firmware and material from the key itself.
Hardware security keys are made by various manufacturers and work with the most popular web browsers, as well as hundreds of apps and online services. They can even help you log in to your workstation. Overall, they’re not hard to use and are relatively inexpensive. And all other forms of two-factor authentication (texts, authenticator apps, and notifications) don’t offer the same level of protection.

How do security keys work?
You can use a single hardware security key for as many accounts as you like. Typically, you insert the security key into your device (or wirelessly connect it) and press a button on the key itself. The security key will then be presented with a challenge by your web browser or app. It will cryptographically sign this challenge, verifying your identity and whatever it is you’re trying to access.
The technical explanation
- Your hardware security key will randomly generate a public and private key pair.
- The private key never leaves your hardware security key.
- But the public key will be sent to a server.
- Your hardware security key will also send a random number (called nonce), which is used to generate your keys, as well as another number (called a checksum), which serves to identify your specific hardware security key.
- When you enter your login credentials into an online account, the server will send that nonce and checksum back to your hardware security key along with a different number.
- The hardware physical key will use the nonce and checksum to regenerate its private key, and then it’ll sign the number that was sent to it by the server, which ultimately verifies and unlocks your online account with your public key.
All this sounds complicated. But it happens in the background without any input from you, other than you inserting the hardware security key into your device. Hardware security keys also use original domains of sites to generate its keys, which means it can’t be tricked by phishing sites.
Supported apps and devices
Many online accounts, apps, services, and websites support hardware security keys, including Twitter, Facebook, Google, Instagram, GitHub, Dropbox, Electronic Arts, Epic Games, Microsoft account services, Nintendo, Okta, and Reddit. Most web browsers do too, like Google Chrome.
Be sure to do your research – look into whether your most-used online accounts and even whether your devices support security keys before you invest in one. You can use hardware security keys to log in to many computers and mobile devices, including Macs, Chromebooks, Windows 10 PCs, and Android and iOS devices. The FIDO2 standard on some security keys can work with Windows Hello and Microsoft’s Edge browser, too.
Lost or stolen security keys
Your hardware security key works in addition to your account login credentials. So, if someone steals your key, they can’t get into your accounts without knowing your logins. Also, if you’ve lost your security key, you can always resort to a backup method of two-factor authentication. You can then gain access to your online account, remove your lost or stolen security key, and either add another or continue using a backup method.

How to set up a security key
All hardware security keys tend to work the same, as we’ve detailed above, but setting them up varies by app and device. To give you an idea of how one works with an online account, we’ve detailed the exact steps for pairing a security key with Facebook and signing into your account.
Using a hardware security key with Facebook
- Log into your Facebook account.
- Click on the drop-down menu icon in the corner and select Settings.
- Now you’re at General Account Settings.
- Select the Security and Login” link from the left sidebar.
- Scroll down until you see the section called Two-Factor Authentication.
- Click Edit on the Use two-factor authentication option.
- Click on Get Started to set up a text message or an authentication app.
- Go back to Two-Factor Authentication and scroll down to Add a Backup.
- Select Setup for the Security Key option.
- Enter your Facebook password and click Submit.
- Connect your security key (usually by inserting it in the USB port).
- Tap the key’s button.
- You should get a confirmation pop-up.
Which hardware security key is the best?
There are several choices to choose from. Yubico, which helps develop is the FIDO U2F authentication standard, is one of the more popular options and has different models available. Google sells its own key, called the Titan, and it includes a spare key with Bluetooth functionality. Other security key manufacturers include Kensington and Thetis.
Here’s our pick of the best ones you can buy:
- Yubikey 5 NFC (USB-A connector with wireless NFC) – View offer at Amazon
- Yubikey 5C (USB-C) – View offer at Amazon
- Yubikey 5 Nano (USB-A) – View offer at Amazon
- Thetis Fido (USB-A) – View offer at Amazon
- Google Titan (one USB-A and one Bluetooth) – View offer at Google
- Thetis BLE (USB-A with Bluetooth) – View offer at Amazon
- Yubikey 5C Nano (USB-C, compatible with Android) – View offer at Amazon
- Kensington Verimark (scanner for Windows Hello) – View offer at Amazon
