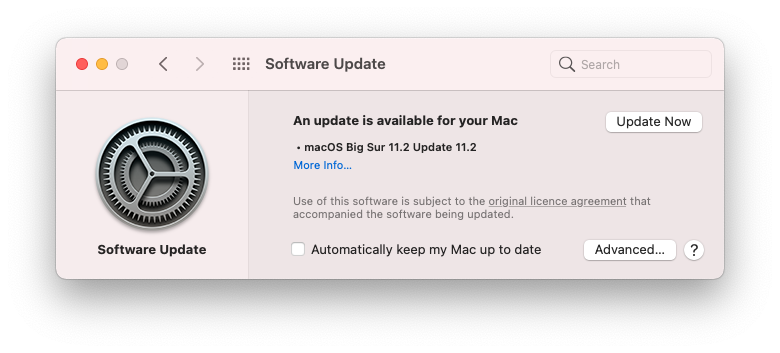
The newest version of macOS Big Sur is macOS 11.2 and it is out now.
There are no significant new functions, but Apple has deactivated the ContentFilterExclusionList that had been allowing Apple apps to bypass third-party firewalls and VPN programs – a potential security risk.
There is also a change that will mean that macOS Big Sur users can’t install iOS apps unless the developer has approved it.
According to Apple’s release notes, the update also addresses problems with Bluetooth and addressing some other small bugs including:
- Fixing an issue with external displays showing a black screen when connected to an M1 Mac mini when connected using HDMI to DVI.
- Edits to Apple ProRAW photos in the Photos app were not always saving.
- iCloud Drive could turn off if the Desktop & Documents option was selected.
- System Preferences might not unlock when a password was entered.
The update is 3.66GB. Alongside this Apple has released a security update for Catalina and Mojave.
Big Sur 11.3 is now in beta. More information: What’s in macOS Big Sur 11.3.
Find out more about Big Sur by reading: macOS 11 Big Sur: latest version, problems & new features for Macs
No bypass
With the arrival of macOS 11.2 Apple’s programs can no longer bypass firewalls such as Little Snitch and VPNs – something the company had been criticised for. Read: Apple’s own programs bypass firewalls and VPNs in Big Sur. Apple has also removed a whitelist for some of its own processes and programs that meant that traffic from these always went straight to the internet.
Installing iOS apps
macOS Big Sur 11.2 also makes changes that will spot users from installing apps that have not been approved by the developer to run on the Mac platform.
This relates to installing iOS apps on M1 Macs. Previously users could download an .ipa file for iPad and install it on their Mac with Apple Configurator 2 or Imazing and thereby run iOS apps on their M1 Mac.
Following the update this will no longer be possible and an error message will read: “This application cannot be installed because the developer did not intend for it to run on this platform.” For more information read: Apple has banned ‘sideloading’ of iOS apps on M1 Macs.
If you need help installing Big Sur read: How to update macOS: Update to Big Sur from Catalina