Windows 10 KB5004945 emergency update is rolling out to address a new Windows zero-day vulnerability called “PrintNightmare”. According to reports, PrintNightmare vulnerability is being actively exploited by attackers to achieve local privilege and remote code execution on affected machines.
Microsoft has now started rolling out out-of-band Windows updates to remedy a PrintNightmare security bug affecting all supported versions of Windows 10.
KB5004945 is a new mandatory security update for those on v2004 or newer. This patch will download/install automatically on Windows 10 Home, Pro and other editions. For those using Windows 10 version 1909 (November 2019 Update), they’ll be getting KB5004946 and this patch will also install automatically depending on update policies.
For Windows 10 version 1809 and Windows Server 2019, there’s a different patch – KB5004947.
List of PrintNightmare updates released for Windows:
- Version 21H1, 20H1, 2004 – KB5004945 (Build 19043.1083).
- Version 1909 – KB5004946 (Build 18363.1646).
- Version 1809 and Windows Server 2019 – KB5004947 (Build 17763.2029).
- Version 1803 – KB5004949
- Version 1507 – KB5004950.
- Windows 8.1 and Windows Server 2012 – KB5004954 and KB5004958 (security only).
- Windows 7 SP1 and Windows Server 2008 R2 SP1 – KB5004953 and KB5004951 (security only)
- Windows Server 2008 SP2 – KB5004955 and KB5004959 (security only).
As mentioned, Windows 10 version 2004 and newer will be getting the following Windows Update when they check for updates today:
2021-07 Cumulative Update for Windows 10 Version 21H1 for x64-based Systems (KB5004945)
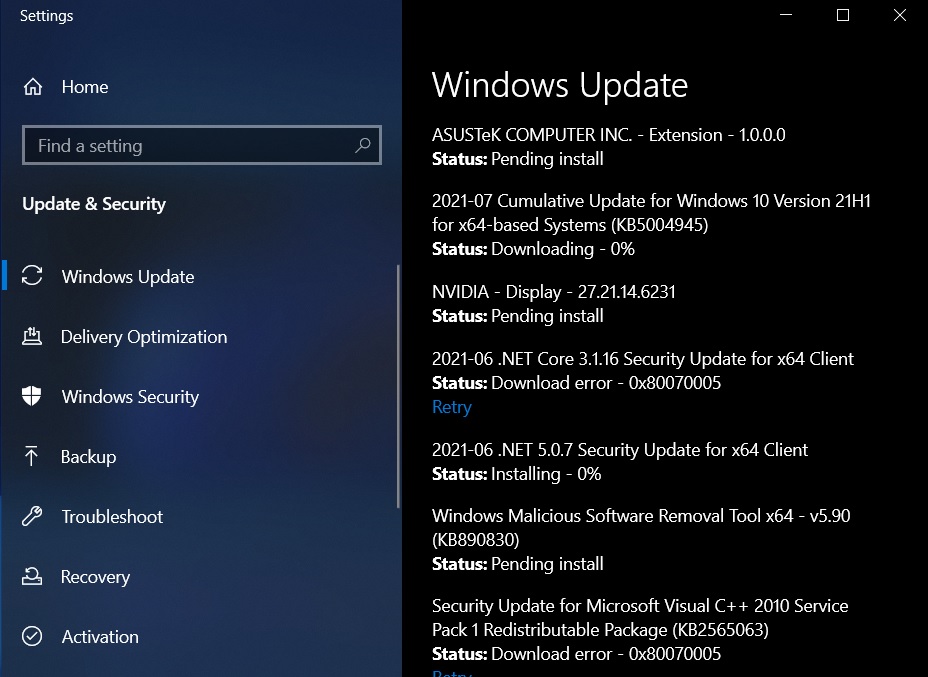
This update will advance the build number to Build 19043.1083 (19042.1083 or 19041.1083).
How to fix PrintNightmare vulnerability on Windows 10
To fix PrintNightmare vulnerability, follow these steps:
- Open Windows Settings > Updates & Security > Windows Update.
- Click on “Check for updates“.
- A new July patch will automatically start downloading on your device.
- Click on “Restart now” after the patch is downloaded.
Alternatively, you can manually download the offline installers from the Microsoft Update Catalog.
Download Links for Windows 10 KB5004945
Windows 10 KB5004945 Direct Download Links: 64-bit and 32-bit (x86).
On Microsoft Update Catalog, you can find offline installers to any Windows Update. To find the update, click on the search box and enter the KB number. Next to the correct version/edition of Windows, click on the “Download” button. This will open a new window in your browser.
To begin the download, copy the .msu link and paste it into another tab.
KB5004945 – Windows PrintNightmare emergency update
The patch consists of various fixes geared towards addressing issues with Windows printer vulnerability that could allow an attacker to bypass the software security protections on affected devices.
The PrintNightmare bug affects Print Spooler which is a service responsible for managing all print jobs for hardware printers or print servers. This feature is enabled default on all Windows machines including Home and Pro editions, and it can be abused by attackers to remotely execute code. If exploited, attackers would gain full access to a domain controller.
Microsoft is advising users to install the emergency on affected devices as soon as possible.
“An Out-of-band update has been released to address a remote code execution exploit in the Windows Print Spooler service. We recommend you update your device as soon as possible,” the company said in a statement.
PrintNighmare vulnerability is also known as CVE-2021-34527 and it does not directly affect Point/Print technology, but it still poses a security threat. For example, it weakens the local security and exploitation could be possible.
In the document, Microsoft explained that installing the emergency Windows Update addresses the critical remote code execution bug in Print Spooler service, and admins can once again apply signed or unsigned printer drivers to a print server.
Here’s a timeline of how the vulnerability was first discovered and reported:
- On June 30, a proof-of-concept (PoC) exploit of the unpatched vulnerability was accidentally posted online, with reports suggesting this issue allows remote code execution.
- On July 1, security agencies issued a warning to enterprises recommending enterprises to disable the Windows Print Spooler service wherever possible.
- On July 2, Microsoft acknowledged the reports and offered workarounds.
- On the same day, reports revealed that attackers have already started actively exploiting the PrintNightmare zero-day after it leaked online. Microsoft recommended users to follow the mitigation measures and prevent attackers from taking over the systems.
- On July 6, Microsoft issued emergency updates for consumers and businesses.
As mentioned at the outset, if you don’t want to install the emergency update, there’s a second workaround – disable Windows Print Spooler service.
How to mitigate Print Spooler PrintNightmae
To disable Print Spooler service to fix the PrintNightmare vulnerability, follow these steps:
- Open Windows Search.
- Type PowerShell and run it as “administrator”.
- Type the following command: Stop-Service -Name Spooler -Force
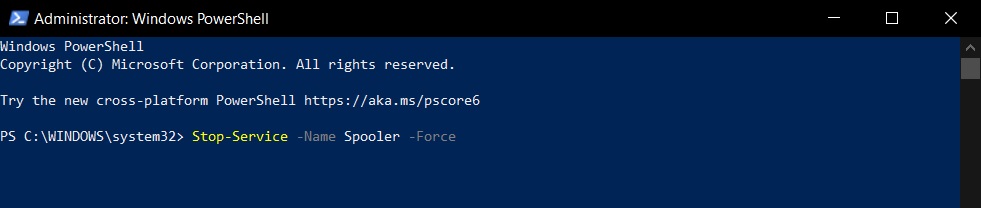
- Press enter.
- Type the following command: Set-Service -Name Spooler -StartupType Disabled
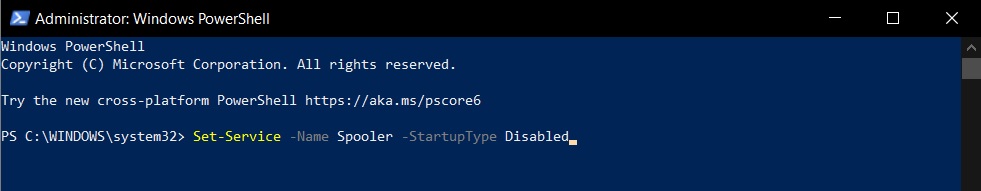
- Press enter.
When you run the above two commands, Windows will disable and prevent the Print Spooler service from starting again. If you want to re-enable the service, run these commands in PowerShell:
- Set-Service -Name Spooler -StartupType Automatic
- Start-Service -Name Spooler
Alternatively, you can mitigate the printing vulnerability by making changes to the Group Policy Editor. To disable the Print Spooler and address PrintNightmare bug, follow these steps:
- Search for gpedit.msc in Windows Search.
- Open the Local Group Policy Editor and navigate to Computer Configuration > Administrative Templates > Printers.
- Select and open Allow Print Spooler to accept client connections policy.
- Select the Disabled option and click on OK
If you want to re-enable the service, follow the above steps again and select “Not configured” or “Enabled”. This will restore the print spooler service and a system reboot is not required.
Remember that these steps should be followed only if you’re planning to skip the out of band update.
Microsoft is currently not aware of any new issues in the emergency patch.
For remaining supported versions of Windows like version 1903, Microsoft is planning to release the emergency patch in the coming days.
If you skip today’s patch, you’ll receive the same fix in July’s Patch Tuesday updates, which will begin rolling out next week (July 13).
The upcoming July Patch Tuesday update is also expected to include a fix for Windows 10’s blurry taskbar bug and issues with News and interests feed. It will also resolve another bug affecting the performance (FPS and graphics quality) of some games, such as Call of Duty and PlayerUnknown’s Battleground (PUBG).
The post Windows 10 KB5004945 emergency update released to fix PrintNightmare appeared first on Windows Latest
